Hislicon CCTV Android Overlay Nightmare: A Comprehensive Critique
Introduction
The widespread deployment of surveillance cameras equipped with Hisilicon chipsets has raised concerns about the potential misuse of this technology for malicious purposes. One such concern is the "Android overlay nightmare," which refers to the exploitation of vulnerabilities in the Android operating system (OS) to gain unauthorized access to the camera's functionality. This essay will critically examine the complexities of the Hisilicon CCTV Android overlay nightmare, exploring its technical and ethical implications, and proposing measures to mitigate its risks.
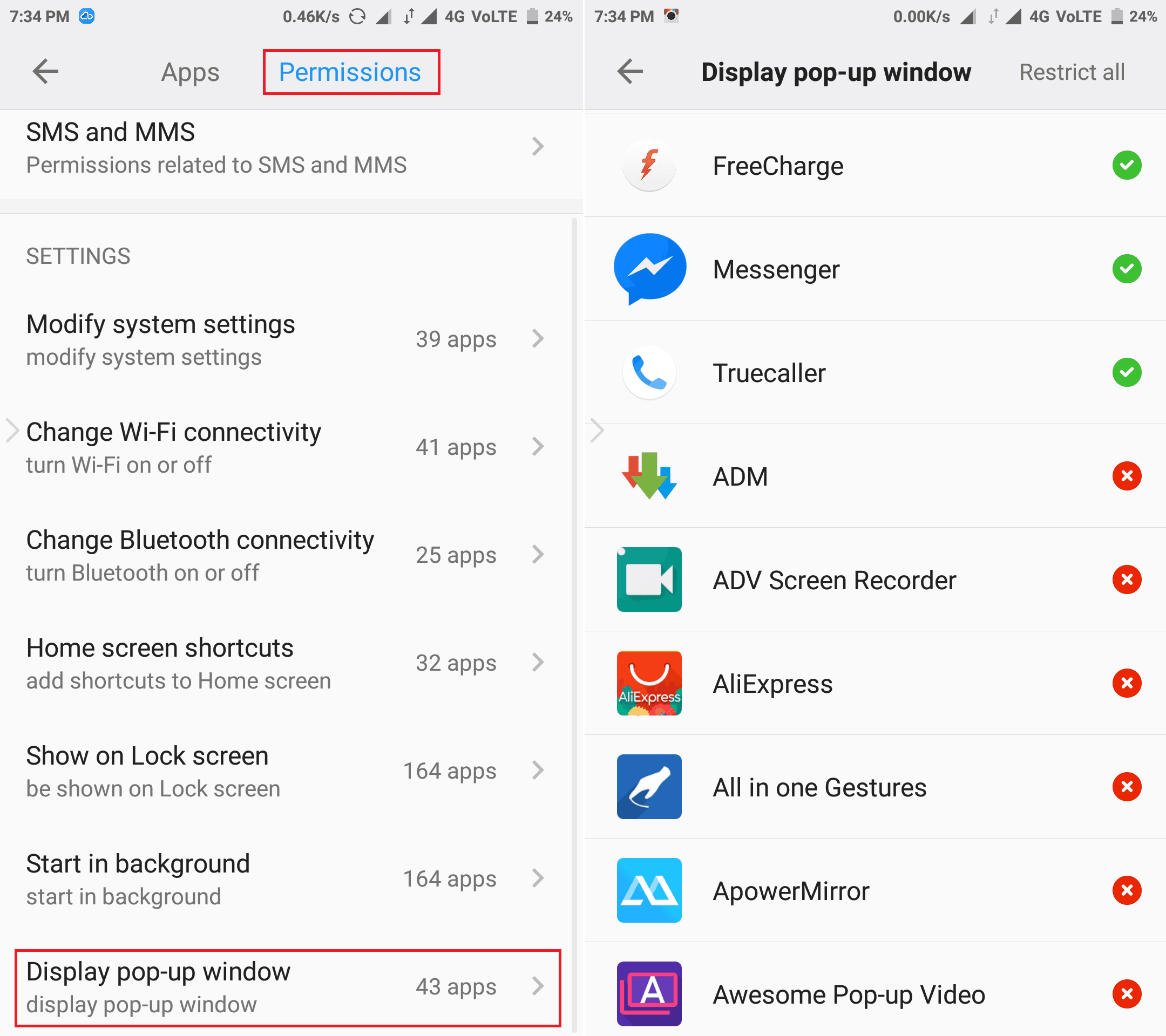
The Hisilicon CCTV Android overlay nightmare exploits vulnerabilities in the Android OS to inject malicious code into the camera's firmware. This code can grant attackers remote control over the camera, allowing them to access the camera's video feed, manipulate its settings, and even record audio. The attackers can use this access to engage in illegal activities such as voyeurism, stalking, and corporate espionage.
The vulnerabilities exploited by the overlay nightmare can be categorized into two main types:
-
Code injection vulnerabilities: These vulnerabilities allow attackers to insert malicious code into the camera's firmware by exploiting weaknesses in the Android OS.
-
Privilege escalation vulnerabilities: These vulnerabilities allow attackers to gain elevated privileges on the camera, giving them access to sensitive data and functions.
Ethical Implications
The Hisilicon CCTV Android overlay nightmare raises several ethical concerns. First and foremost, it violates the privacy of individuals by enabling unauthorized access to their private spaces. This violation of privacy can have severe consequences for victims, including emotional distress, psychological trauma, and even physical harm.
Second, the overlay nightmare raises concerns about data security. Attackers who gain access to a camera's video feed can collect sensitive information about individuals, such as their daily routines, social interactions, and personal habits. This information can be used for malicious purposes such as blackmail, extortion, or identity theft.
Third, the overlay nightmare has the potential to compromise critical infrastructure. Hisilicon CCTV cameras are widely used in public spaces, such as schools, hospitals, and government buildings. If these cameras are compromised, attackers could gain access to sensitive information about these facilities, potentially leading to disruption of operations or even security breaches.
Mitigating Risks
Several measures can be taken to mitigate the risks associated with the Hisilicon CCTV Android overlay nightmare.
-
Vulnerability patching: Camera manufacturers should regularly release security patches to address vulnerabilities in the Android OS. These patches should be applied as soon as possible to protect cameras from exploitation.
-
Strong password protection: Camera users should use strong, unique passwords for their camera accounts. This makes it more difficult for attackers to gain unauthorized access to the camera.
-
Use of encrypted communication channels: Camera manufacturers should use encrypted communication channels to transmit video and audio data. This prevents attackers from eavesdropping on the camera's communications.
-
Physical security measures: Cameras should be installed in secure locations where unauthorized access to the camera's hardware is restricted.
-
Regular security audits: Camera systems should be regularly audited by qualified security professionals to identify and address any potential vulnerabilities.
Conclusion
The Hisilicon CCTV Android overlay nightmare is a serious security issue that poses significant risks to privacy, data security, and critical infrastructure. By understanding the technical and ethical implications of this issue and implementing appropriate mitigation measures, we can help to protect ourselves from the malicious use of surveillance technology.
Furthermore, governments and industry regulators should play a role in addressing this issue by enacting regulations that require camera manufacturers to adhere to best practices for cybersecurity. They should also promote awareness of the risks associated with the Hisilicon CCTV Android overlay nightmare and provide guidance on how to mitigate these risks.
By taking these steps, we can help to ensure that surveillance technology is used for its intended purpose: to enhance security and protect the public, not to violate privacy or compromise our safety.
Fantasy Football Meltdown: ESPN's Rankings Just Blew Up!
Is Your Postgres JSONB GIN Index A Lie? Performance Troubleshooting Guide
Is BMP-24-740 The Future? Experts Weigh In